- MindByte Weekly Pulse: Weekly IT Insights: Quick GitHub, Azure, & .NET Updates
- Posts
- MindByte Issue #38: GitHub Unveiled: Security, Workflow, and the Future of Open-Source Monetization
MindByte Issue #38: GitHub Unveiled: Security, Workflow, and the Future of Open-Source Monetization
What's New in GitHub: Breaking Down the Updates You Can’t Afford to Miss in Security, Workflows, and Open-Source Economics.
Introduction
Welcome to Issue 38 of MindByte Weekly Pulse! Here, I bring you the latest buzz in the tech world, with a particular focus on GitHub, .NET, and Azure. Whether you're a seasoned developer or just starting out, there's something here to fuel your curiosity and passion for technology.

Let's dive right in, shall we?
Pulse of the week
This week the spotlight is on GitHub's continued efforts to make developers' lives easier and more secure. From enabling seamless management of multiple accounts on mobile to introducing workflow-boosting features like Codespaces templates, GitHub is leaving no stone unturned. The unveiling of GitHub Advanced Security (GHAS) shows an integrated approach towards security without sacrificing productivity. Add to this the cautionary tales of misconfigurations and you've got a complete package that emphasizes both efficiency and security.
These advancements signal a paradigm shift in how we approach development workflows and security protocols. It’s not just about coding anymore; it's about doing so in an environment that is robust, secure, and incredibly efficient.
So, if you haven't dived into these updates yet, now's the time. They could just be the game-changers you've been waiting for.
GitHub Digest
Manage Multiple GitHub Accounts Seamlessly with GitHub Mobile
Ever find yourself switching back and forth between your work and personal GitHub accounts? GitHub Mobile has now introduced support for multiple accounts, making life a whole lot easier. You can now log in with both accounts, swap effortlessly, and even receive push notifications tailored to each. All while keeping your data distinct and secure.
Simplify Your Dev Setup with GitHub Codespaces
Tired of the cumbersome setup process for new coding projects? GitHub Codespaces could be the solution you didn't know you needed. This cloud-based coding environment allows you to eliminate the headache of configuring build settings and dependencies.
Dive into the article to discover how to create custom templates for your projects, whether you're developing an Android app or working in another ecosystem.
Find out how to streamline your workflows and focus on what really matters: writing exceptional software. Don't miss this opportunity to make your coding life easier and more productive.
Supercharge Your Security with GitHub Advanced Security
In today's interconnected software landscape, striking a balance between security and productivity is a challenge. Traditional methods often involve using multiple, disparate security tools, which can disrupt workflows and hinder collaboration.
Enter GitHub Advanced Security (GHAS), designed to integrate security directly into your existing GitHub workflows. From automated code scanning on every pull request to identifying insecure code patterns and leaked credentials, GHAS offers a seamless developer experience. With features like CodeQL, Dependabot, and over 60 third-party integrations, it promises a unified security testing process without sacrificing productivity.
Read on to discover how GHAS can revolutionize your AppSec program while keeping you in the familiar grounds of GitHub.
New Feature Alert: Boost Your Workflows with Repository Actions Runners List
GitHub is making strides in simplifying your workflow with the public beta release of the Repository Actions Runners List feature. Now, you can view all available runner types—Standard, Larger, Self-hosted, and Scale-sets—directly from the Actions tab of a repository.

Key Features:
Improved Visibility: Users with repo:write access can now view runner options without needing to rely on internal documentation or contact repo admins or Organization owners.
Faster Access to Runner Labels: Quickly view and copy labels for all runners, making it straightforward to identify the type of runner you need and use it in a workflow.
Available to Free and Pro Personal Accounts, as well as Paid Organizations on specific plans, this feature promises to make your GitHub experience even more seamless.
GitHub Security Alert: The Risks of Misconfiguration and How to Avoid Them
A recent security breach highlighted the importance of proper configuration and the role of bug bounty programs in ensuring corporate cybersecurity. Security researcher Corben Leo uncovered admin-level GitHub credentials from a well-known car company, revealing significant lapses in their security protocols.

How the Breach Happened:
1. Misconfigured Spring Boot Actuator: Corben Leo, participating in a bug bounty program, identified vulnerabilities in a Spring Boot Actuator that was part of the car company's Kubernetes environment. The misconfiguration exposed HTTP endpoints /env and /heapdump.
2. Exposed Plaintext Passwords: While the /env endpoint had redacted passwords, the /heapdump endpoint provided snapshots of objects stored in memory, revealing plaintext credentials. Corben leveraged these to gain broader access, finding another set of exposed endpoints with unredacted credentials.
3. Overly Broad Access: Ultimately, Corben found that the exposed GitHub credentials provided admin-level access to over 30 organizations and hundreds of repositories.
The Risks:
1. Misconfiguration Risks: Misconfigurations, especially in Infrastructure as Code (IaC) setups, can multiply across instances if not detected early.
2. Credential Exposure: The plaintext storage of passwords and secrets can create catastrophic vulnerabilities.
3. Overly Permissive Roles: Admin credentials with excessive permissions can expose multiple repositories and organizations to significant risk.
How to Secure Against Similar Attacks:
1. Early IaC Scanning: Employ tools like GitGuardian’s Infra as Code Security module to catch misconfigurations early in the process.
2. Check for Secrets Everywhere: Employ tools that can scan not only your code but also any logs or files that the code produces. Ensure that passwords are never stored in plaintext.
3. Apply the Principle of Least Privilege: Use credentials that are tightly scoped for their intended purpose, limiting permissions to what is absolutely necessary.
This incident serves as a cautionary tale, emphasizing the importance of robust security measures and constant vigilance. Participating in bug bounty programs and maintaining stringent security protocols can help prevent such mishaps in the future.
Protect your repositories. Discover the full story below.
GitHub: The Missing Link in Open Source Monetization?
Ever wondered why open-source projects, despite their widespread usage, often struggle to monetize effectively? Ayende Rahien, a developer with two decades of experience in open-source work, sheds light on this conundrum. According to him, the donation model for open-source projects is fundamentally flawed. While developers might want to donate, the pathway to actually doing so is riddled with obstacles. For companies, it's even more complicated, involving approvals, justifications, and an array of tax implications.
Ayende suggests that effective monetization requires treating an open-source project like a commercial endeavor. This means having a well-defined pricing strategy and enforcing limitations that create an incentive to purchase a license. The key challenge? Making the payment process less of a Herculean task.
This is where GitHub could step in. GitHub is well-positioned to act as a "payment pipe," streamlining the invoicing and payment collection process for open-source projects. Most organizations are already set up with GitHub, making it a convenient medium for straightforward transactions. Although not a magic bullet solution, this approach could significantly lower the barriers to financial sustainability for open-source projects.
So, could GitHub be the game-changer in how open-source projects find their footing in the commercial world? It's a question worth exploring as we look for ways to balance the scales between open-source generosity and financial viability.
Coding Corner
OpenFeature – A Step Towards Standardized Feature Flagging
Stumbled upon something cool that's worth sharing with you all—OpenFeature. But first, a quick rundown on feature flags.
What's a Feature Flag?
For those who might be unfamiliar, feature flags are a nifty development technique that allows teams to turn features on or off, or alter their behavior, without having to modify the source code. It's an incredibly flexible way to test, deploy, and manage your application features.
Introducing OpenFeature
OpenFeature aims to standardize this practice. It offers a vendor-agnostic, community-driven API for feature flagging, which can work in harmony with your preferred feature flag management tool. Imagine not being tied down to a specific vendor and being able to switch your feature flagging system as you please—OpenFeature makes this possible.
Why Standardize Feature Flagging?
Standardization brings a plethora of benefits. It fosters a unified approach by consolidating various tools and vendors behind a common interface. This eliminates the dread of vendor lock-in at the code level and paves the way for reusable extensions and integrations that can benefit the broader community.
Curious to dive in? Here's the link to OpenFeature to learn more and perhaps, contribute to the standardization of feature flagging.
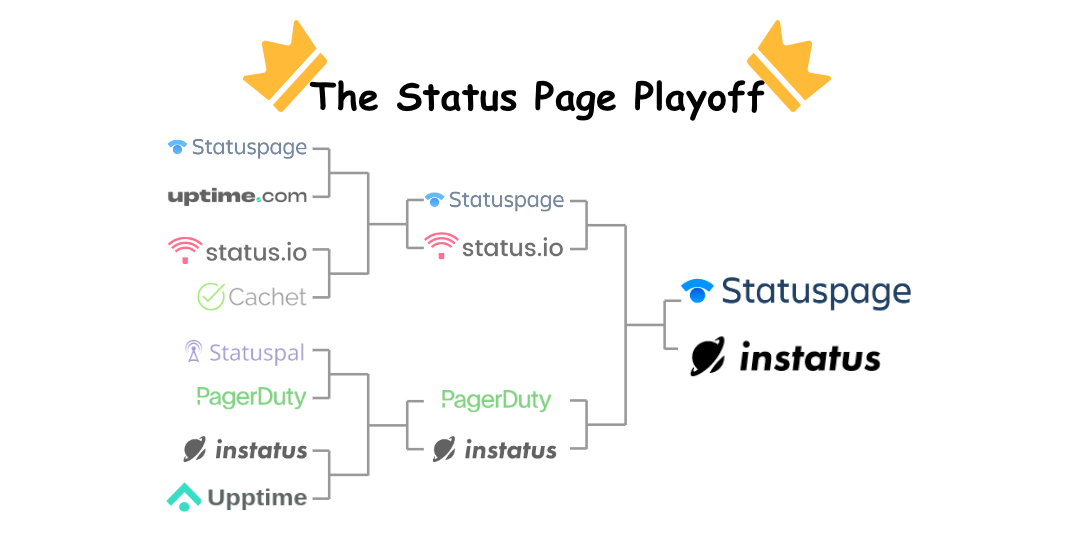
Decoding the Decision-Making: A Guide to Selecting a Status Page Vendor
The real gem of this article isn't the ultimate pick of Instatus as the top status page vendor; it's the detailed decision-making process behind that choice.
The writer starts by setting a crystal-clear objective: finding the best status page for a mid-sized startup. Knowing what you aim to achieve is half the battle.
Next up, a comprehensive list of requirements is established. This isn't about what the market offers; it's about what you need.
The writer then sorts through 11 different vendors across three rounds based on:
Essential features
Depth of offerings
Hands-on experience
Last but not least, hands-on experience is invaluable. Set up trials, click buttons, and see for yourself how these services function in real-world settings.
In summary, a well-defined goal, clear requirements, rigorous evaluation, and firsthand experience are the pillars of good decision-making.
Curious to see the full article? Check it out below.
Do you have any thoughts on this decision-making framework? I'd love to hear them!
Are Your Meetings Really Necessary?
We all know the drill: back-to-back meetings that leave us questioning if we're actually getting any real work done. Meetings are a universal experience in the developer world, often crowding out time for focused, individual tasks. But how many of these meetings are truly essential?
If you find yourself navigating a labyrinth of Zoom calls and conference rooms, this article is a must-read. It offers a simple but effective system to evaluate the necessity and productivity of your meetings. Trust me, your calendar will thank you.
Azure Updates & Insights
Are You Struggling with Escalating Cloud Costs? You're Not Alone.
As someone deeply interested in FinOps (Financial Operations), alongside my regular coding pursuits, I find the topic of managing cloud costs a crucial yet often overlooked issue in today's tech ecosystem. According to Gartner, companies are projected to spend an eye-watering $600 billion on public-cloud services in 2023. Companies like Netflix, Twitter, and Airbnb are publicly scrambling to rein in their escalating cloud expenditures, prompting serious discussions in boardrooms across industries.
Despite glaring warning signs, many organizations find themselves trapped in a cycle of "optimize later," much like the "patch later" mentality that plagued software security years ago. This mindset has led companies to build cost-inefficient infrastructure, only to attempt Band-Aid solutions afterwards. As a result, some experts predict a spate of business failures in 2023 due to reckless cloud spending.
The article I'm sharing today delves deep into the roots of this denial, drawing parallels to Microsoft's "Trustworthy Computing" initiative of 2002, which radically shifted the company's approach to software security. Just as security had to become an engineering priority, today's cloud cost challenges must be tackled at the root—by engineers, not just finance teams.
If you're grappling with skyrocketing cloud costs and are looking for a way out of the quagmire, this is a must-read.
.NET Nook
Simplifying Azure Cost API Authentication Within Azure Cost CLI
If you've been working with Azure APIs, you know that authenticating against the API can be a stumbling block for usage. That's why I've penned a recent blog post to guide you through the process of getting that essential token for API access.

Security is not always this simple
Don't let API authentication slow you down; head to my blog to find out how to streamline it:
Sisk: A Fresh Alternative for HTTP Servers in the .NET World
Sisk is an HTTP server that exists independently of ASP.NET Core, offering a lightweight and straightforward programming model. It's 100% open-source, multi-platform, and written in C#. It includes features such as routing, request handling, middleware, logging, web sockets, and more—all without requiring ASP.NET Core.
Let's look at how to create a simple two-endpoint HTTP server using Sisk.
using Sisk.Core.Http;
using static Sisk.Core.Routing.RouteMethod;
var http = HttpServer.Emit(insecureHttpPort: 5000, host: out , configuration: out , router: out var router);
router.SetRoute(Get, "/", _ => new(200) {
Content = new StringContent("Hello, World")
});
router.SetRoute(Get, "/hi/<name>", req => {
var name = req.Query["name"];
return new(200) {
Content = new HtmlContent($"<h1>Hello, {name}</h1>")
};
});
http.Start();
Console.WriteLine($"HTTP Server is listening on {http.ListeningPrefixes[0]}");
Console.ReadKey();Sisk is a welcome addition to the .NET ecosystem, particularly if you're looking for an HTTP server outside the ASP.NET Core paradigm. It's worth checking out whether you're building a local application, working on microservices, or just want to experiment with a new HTTP server model.
For an in-depth look at Sisk, read the full article:
Closing Thoughts
Thank you for taking the time to read this week's edition of the newsletter. I hope you found the insights and updates invaluable. If you haven't already subscribed, I invite you to do so to keep your finger on the pulse of all things tech.
I'd love to hear your thoughts, so feel free to react or drop a comment. Until next week, happy coding!







Join the conversation